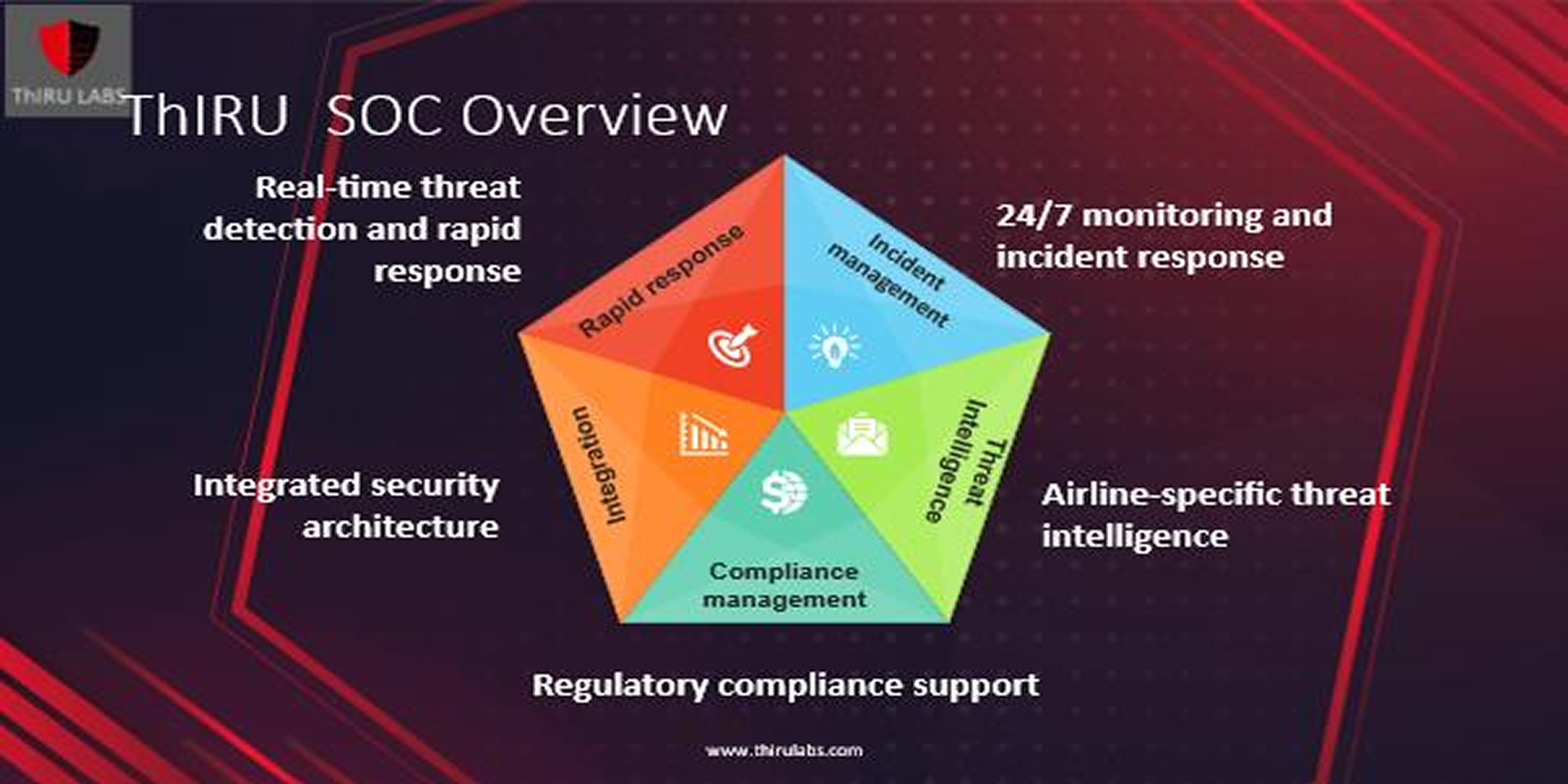
ThIRU = ICU for Cyber Threats
Monitoring from endpoint to edge device. Complete cyber security solutions in a single platform built on the principles of Zero Trust Architecture (ZTA).
Backed by professional services
- Secure access [Access Control]
- Manage employees [Identity Management]
- One click secure login [Single Sign-On (SSO)]
- Manage laptops & desktops [Malware / Ransomware protection]
- Regular machine cleanup [Device hygiene]
- Regular machines and software update [Patching]
- Sensitive data protection [Data encryption & Vault]
- Control USB data transfers [USB port block]
- Wi-Fi network protection [IDS-IPS]
- Email phishing/spam protection
- Secure data storages [Regular cloud backup]
- Check vulnerabilities[Vulnerability scanning and reporting]
- Check applications & fix loopholes [Penetration testing]
- Service desk and ticketing
- Cyber consultation
- Cyber Audits including ISO27001 & Essential 8